In this example, we will look at another malicious DLL (obe.dll). The following screenshot shows two functions (DllRegisterServer and DllUnRegisterServer) exported by the DLL:
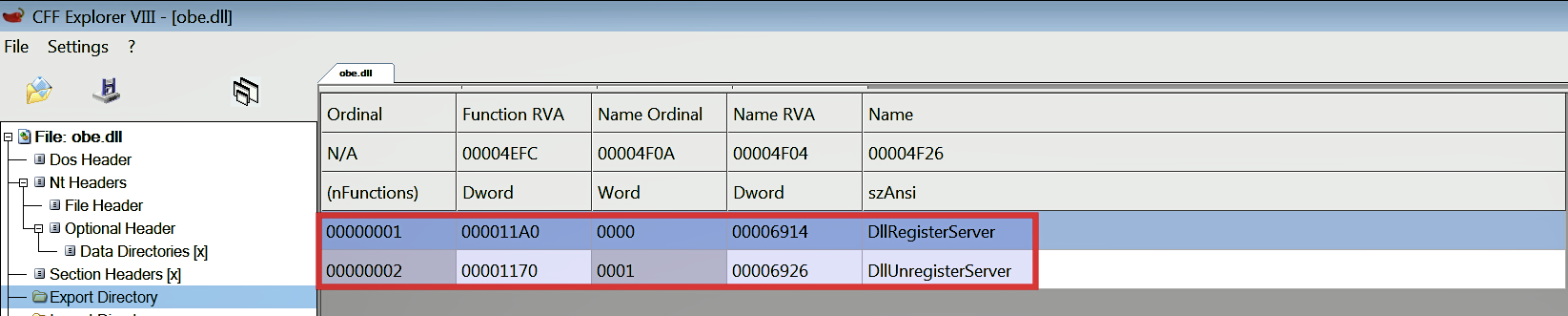
The DLL sample was run with the following command. Even though obe.dll was loaded into the memory of rundll32.exe, it did not trigger any behavior. This is because DLL's entry point function does not implement any functionality:
C:\>rundll32.exe c:\samples\obe.dll,test
On the other hand, running the sample with the DllRegisterServer function as shown below, triggered an HTTPS communication to the C2 server. From this, it ...

