Device logs leaking application sensitive data
Many times, application logs the input data to ease the debug process. Now, if an application is logging sensitive information, then its data will be captured on device logs. An attacker can easily dump device logs and retrieve the user's sensitive information.
Let's follow the given steps to capture device logs that are leaking sensitive information:
- You can use the Organizer utility provided with Xcode. Connect the iDevice to Mac, start the Organizer and dump the device logs:
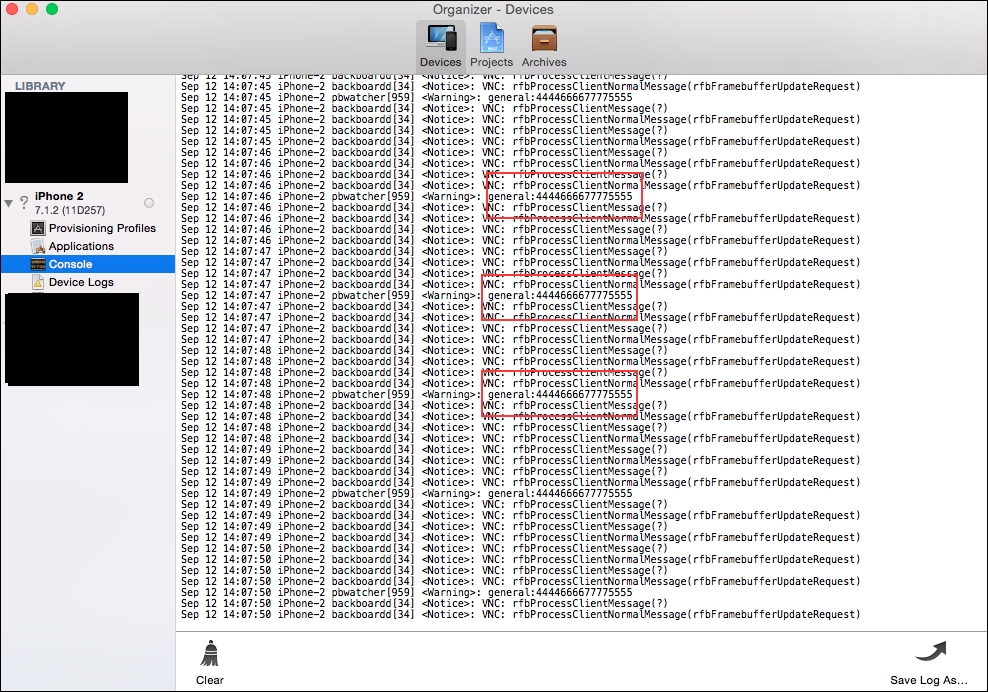
- You can automate this process using the idb tool. Use the Log option to capture all device logs and check whether the iDevice ...
Get Learning iOS Penetration Testing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

