iOS secure boot chain
The iOS secure boot chain system uses secure boot chain mechanism to provide security in the booting process. We have seen many rootkits and malware that infect at boot level. The iOS secure boot chain ensures that low-level software is not compromised and iOS is running on validated iDevice.
The following figure is the block diagram for an iOS secure boot chain:
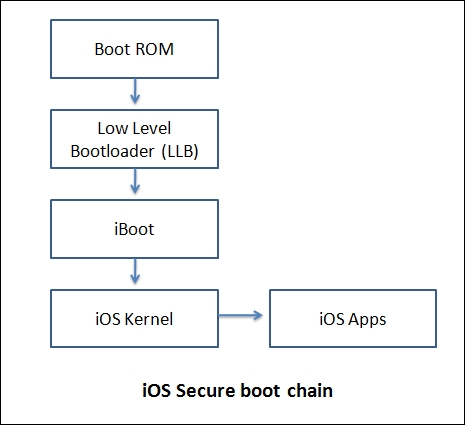
Let's study iOS secure boot chain step by step, as follows:
- Boot ROM
- This is implicitly trusted
- It is known as a hardware root of trust
- This code is contained in the processor and cannot be updated or changed
- This also contains the Apple root certificate with authentic public ...
Get Learning iOS Penetration Testing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

