One of the most explanatory social engineering attack life cycles, among many offered, is the one proposed as follows, refer to point 8 under the References section. :
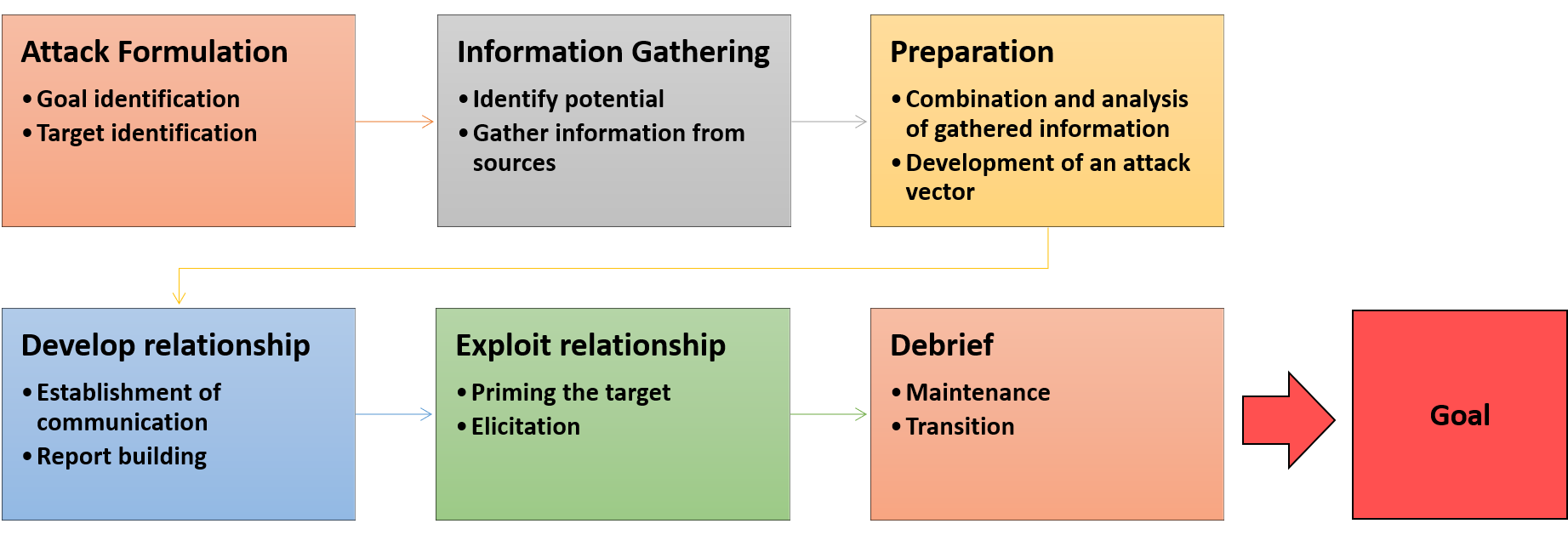
The paper introduces new social engineering attack life cycle which includes the following steps: Attack Formulation, Information Gathering, Preparation, Developing relationship, Exploit relationship, and Debrief. Refer to point 8 under the References section, for more information on this model.

