Time for action – AP-less WPA cracking
- We will set up a WPA-PSK Honeypot with the ESSID Wireless Lab. The
-z 2option creates a WPA-PSK access point, which uses TKIP: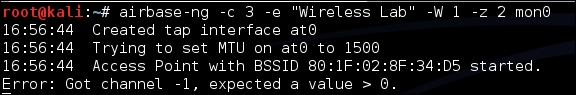
- Let's also start
airodump-ngto capture packets from this network:
- Now when our roaming client connects to this access point, it starts the handshake but fails to complete it after Message 2, as discussed previously; however, the data required to crack the handshake has been captured.
- We run the
airodump-ngcapture file throughaircrack-ngwith the same dictionary file as before; eventually, ...
Get Kali Linux Wireless Penetration Testing : Beginner's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

