Time for action – deauthenticating the client
Follow these instructions to get started:
- Let's first bring our access point Wireless Lab online again. Let's keep it running on WEP to prove that, even with encryption enabled, it is possible to attack the access point and client connection. Let's verify that the access point is up using
airodump-ng: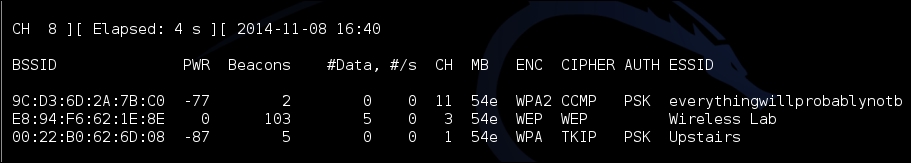
- Let's connect our client to this access point and verify it with
airodump-ng: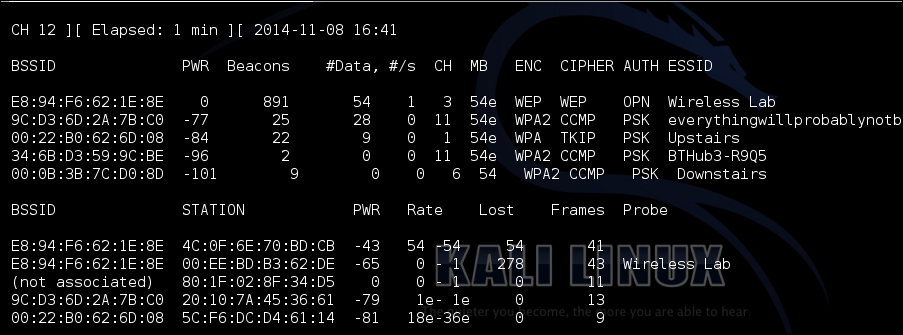
- We will now run
aireplay-ngto target the access point connection: - The client gets disconnected and tries to reconnect to the access ...
Get Kali Linux Wireless Penetration Testing : Beginner's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

