Time for action – cracking WPA-PSK weak passphrases
Follow the given instructions to get started:
- Let's first connect to our access point Wireless Lab and set the access point to use WPA-PSK. We will set the WPA-PSK passphrase to
abcdefghso that it is vulnerable to a dictionary attack: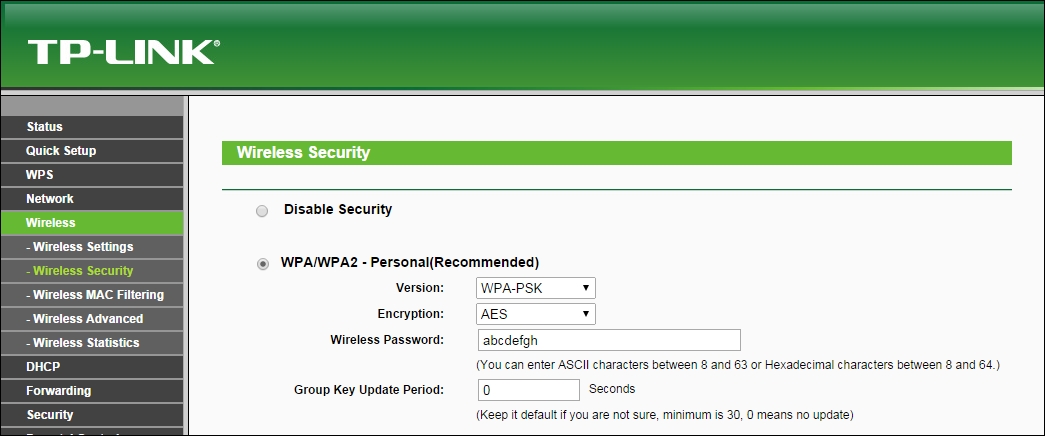
- We start
airodump-ngwith the following command so that it starts capturing and storing all packets for our network:airodump-ng –bssid 00:21:91:D2:8E:25 –channel 11 –write WPACrackingDemo mon0"The following screenshot shows the output:
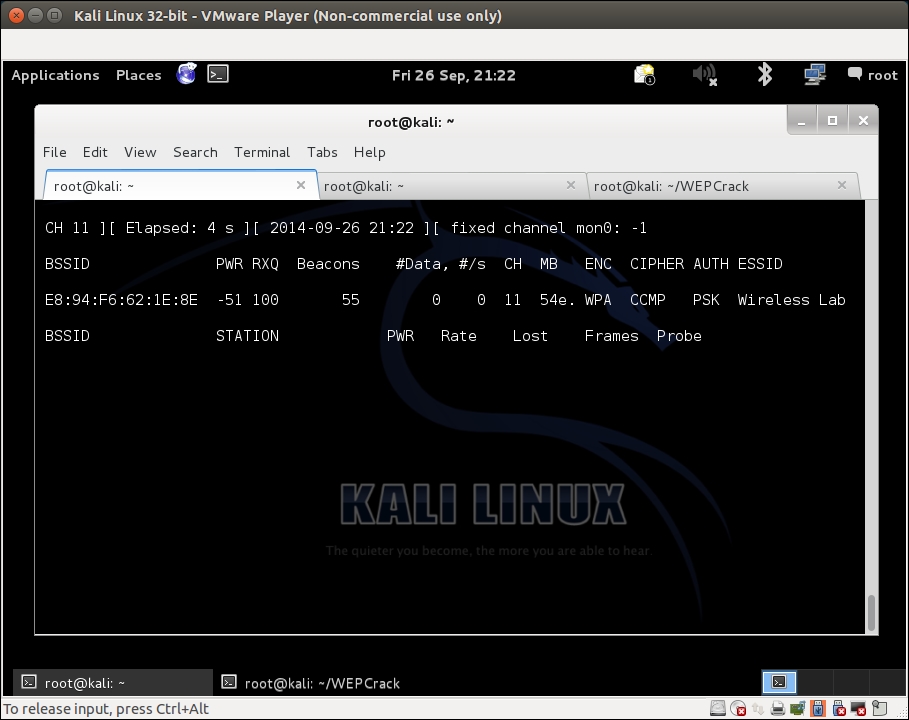
- Now we can wait for a new client ...
Get Kali Linux Wireless Penetration Testing : Beginner's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

