Configuring User Accounts
In the previous section, a trace file was set up that was “world-readable” so that anyone who managed to log in to the device successfully could read the file. However, by default, only a certain set of users can view trace files (if you put all users into this user set, of course, then all users who access the devices can read the trace files). In this section, you find out how users can be set up to have a greater or lesser number of capabilities, or privileges.
Sets of users with their privileges are called classes, and four standard login privilege classes exist on a Junos OS device, as shown in Table 6-3.
Table 6-3 Standard Login Privilege Classes
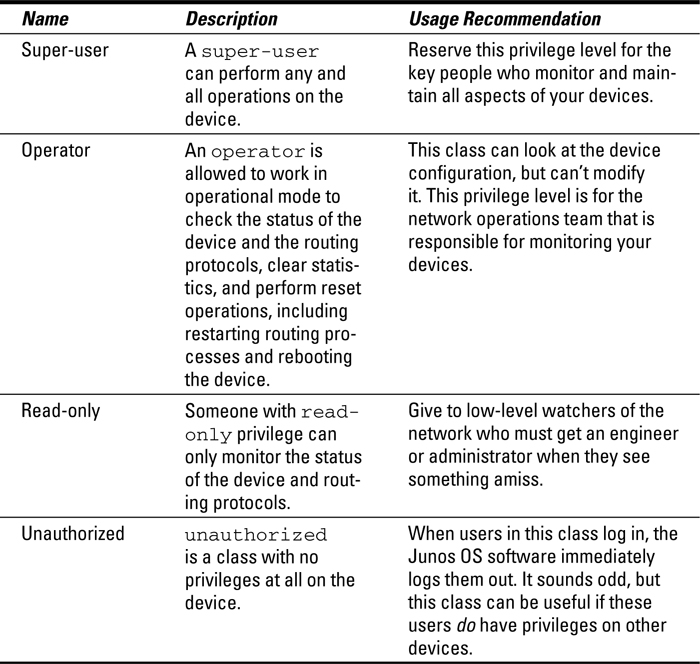
You may be tempted to put every valid user into the super-user class and be done with it, but doing so is usually a big mistake. Super-users can do literally everything, including granting super-user privileges to other users. One well-known trick is to quickly log in as a super-user and create an innocent-looking user ID (“guest-1”) that also just happens to have super-user privileges and log out again. But the damage is done.
Everyone will claim they can't do their job unless they have super-user privileges. This is nonsense, and a bit like saying you can't write a book unless you have superpowers and a red cape (then again, that would be really neat). Save your super-user class for people who really need ...
Get Junos® OS For Dummies®, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

