Securing Access to the Router
The goal of this chapter is to secure the network in Figure 8-2, which consists of three routers—Ale, PBR, and
Bock—that are running Open Shortest
Path First (OSPF) as the Interior Gateway Protocol (IGP). PBR connects to multiple Internet service
providers (ISPs) via the Border Gateway Protocol (BGP). Various types of
traffic are sent and received from the two ISPs, including web browsing,
email, and a variety of remote accounting and engineering applications.
The first step will be to secure access to Ale, PBR, and
Bock so that only authorized users have
access to each router.
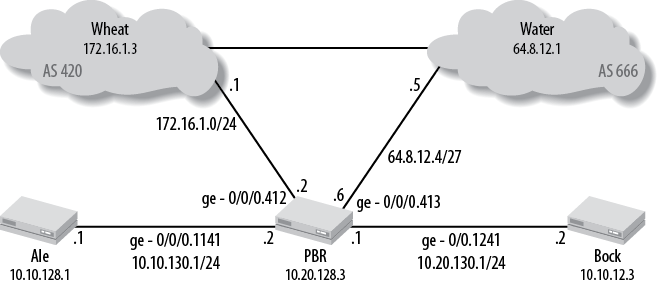
Figure 8-2. Network topology
User Authentication
There are two types of users on a Junos-based device—a nonroot user and
a root user, both of which must be secured. Recall that user root is the
only user who is predefined by default, accessible only via the console
port without any default password. You must set a root password before
the router will allow you to commit the configuration. To set up a
root password, issue the root-authentication
keyword under the [edit system] level:
lab@Bock# set system root-authentication ? Possible completions: + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups encrypted-password Encrypted password string load-key-file File (URL) containing one or more ssh keys plain-text-password ...Get Junos Enterprise Routing, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

