A Key Management Example
Now we’ll proceed to a framework for enterprise-wide key
management. Figure 10-1 shows the role of the
keystore in the creation and execution of a signed jar file.
Thejarsigner
utility consults
the keystore for the private key of the entity that is signing the
jar file. Once the signed jar file is produced, it is placed on a web
server, where it can be downloaded into an
appletviewer or the Java Plug-in. When the jar
file is read on the remote system, the keystore is consulted in order
to retrieve the public key of the entity that signed the jar file so
that the jar file’s signature can be verified.
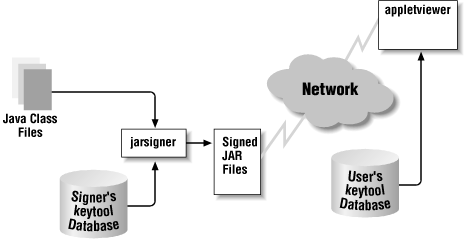
Figure 10-1. the keytool database in a signed JAR file
Note that the two keystores in this example are (probably) separate files on separate machines. They probably have completely different entries as well -- even for the entry that represents the signer. The signer’s entry in her own database must have the private key of the signer while the signer’s entry in the user’s database needs only a certificate for the signer. However, the keystore could (in this and all examples) be a shared database.
Since access to the private key of the signer is protected by a password, the signer and the end user are able to share a single database without concern that the end user may obtain access to the signer’s private key (assuming that she keeps her password secret, of course). ...
Get Java Security, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

