Appendix E
Cracking WEP Keys Using WEPCrack
This appendix describes an experiment to crack a WEP-protected WLAN using WEPCrack, an open-source WEP cracking tool. WEPCrack implements the RC4 weak-key attack introduced in 2001 by Fluhrer, Mantin, and Shamir. It is written in the Perl language. Stephen Brinton designed and implemented the experiments.
E.1 System Setup
The experiment uses three computers and one WEP-enabled Linksys wireless router as an AP. One computer serves as an Apache Web server, which is connected to the router via an Ethernet cable. The second computer is a WEP-enabled wireless laptop PC connected to the router. The router and the laptop computer share a 104-bit secret WEP key ![]() . This computer continuously requests Web pages from the Web server for the purpose of generating a large number of frames. The third computer is also a laptop PC equipped with a WEP-enabled wireless network interface card (NIC) that can monitor network traffic. This computer runs WEPCrack to crack the WEP key
. This computer continuously requests Web pages from the Web server for the purpose of generating a large number of frames. The third computer is also a laptop PC equipped with a WEP-enabled wireless network interface card (NIC) that can monitor network traffic. This computer runs WEPCrack to crack the WEP key ![]() . Figure E.1 shows the system setup of this experiment.
. Figure E.1 shows the system setup of this experiment.
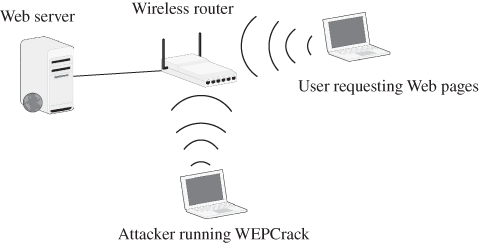
Figure E.1 WEPCrack experiment system setup
The experiment uses the following AP and wireless NICs:
AP
The AP used in the ...
Get Introduction to Network Security, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

