In-Depth ExampleâDirectory Listings
This example shows how the careful study of directory listings can uncover important clues that link a phishing site to a series of quite different scams. The trigger for this investigation was an email that appeared to come from First USA Bank, requesting that I log into their site and enter my credit card details.
The link took me to a fake login page at the domain 1stusa.info, which has no connection to the
real bank. The site looked like a typical phishing attempt and seemed to
be of little interest, until I started looking at directory listings.
The HTML source of the login page showed that the bank logo and other
images were located in the /images/
directory. Entering the URL http://1stusa.info/images/ brought up an extensive
directory listing, of which a small section is shown in Figure 5-4.
A number of these images were used in the login page, but most were not. As the directory listing includes links to the files, I was able to see what these other images represented, which made for some extremely interesting browsing. For example, the
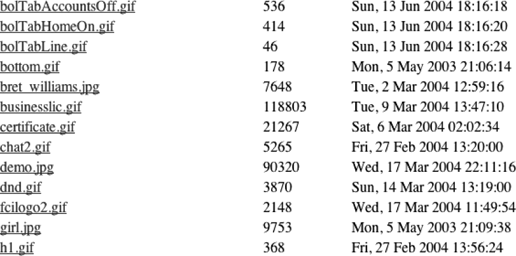
Figure 5-4. Section of a directory listing from a phishing site
file welcome.jpg was an image with the text âWelcome to International Checkbank!â and demo.jpg was a screenshot of two web forms that related to check cashing and wire transfers on a site called http://checkbank.com. The image fcilogo2.gif ...
Get Internet Forensics now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

