Policy Management
Once you perform your risk assessment and you’ve begun the information security and risk management conversation, the next step is to take a look at your information security policy set.
Keywords
Information Security Policy; Data Classification Policy; Acceptable Use Policy
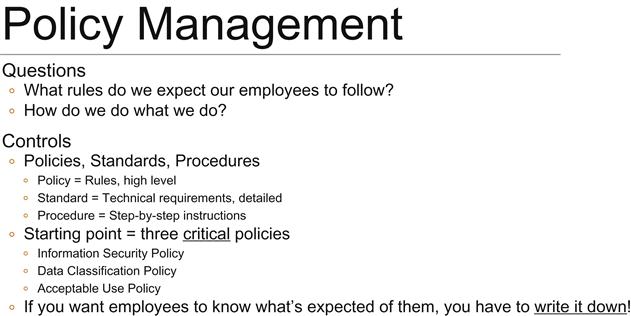
Once you perform your risk assessment and you’ve begun the information security and risk management conversation started, the next step is to take a look at your information security policy set.
The questions to ask at this stage:
What are the rules that we expect our employees to follow?
If you are going to work at our company, what’s okay and ...
Get Infosec Management Fundamentals now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

