Chapter 6Basics of Cyber security
In a modern environment, there are several types of communications: wire (plant and outside telephone), fiber optic (data and voice), radio (pagers and mobile radios), and satellite upload and download links. All are susceptible to interference and attack including tapping and monitoring (may be illegal, but when has that stopped anyone with mal intent?), signal interruption (jamming, cutting lines, establishing false commands), spoofing and misdirection (think radio commands and requests for assistance or misdirection), and introduction of viruses, worms, etc. through these channels into the other hardware and software that operate both analog and digital equipment.
Communications Life Cycle
All communications security goes through a life cycle, and this life cycle is only a slight modification of the basic security life cycle, which has been presented before in a previous chapter. It indicates the need for continuous review and improvement (Fig. 6.1).
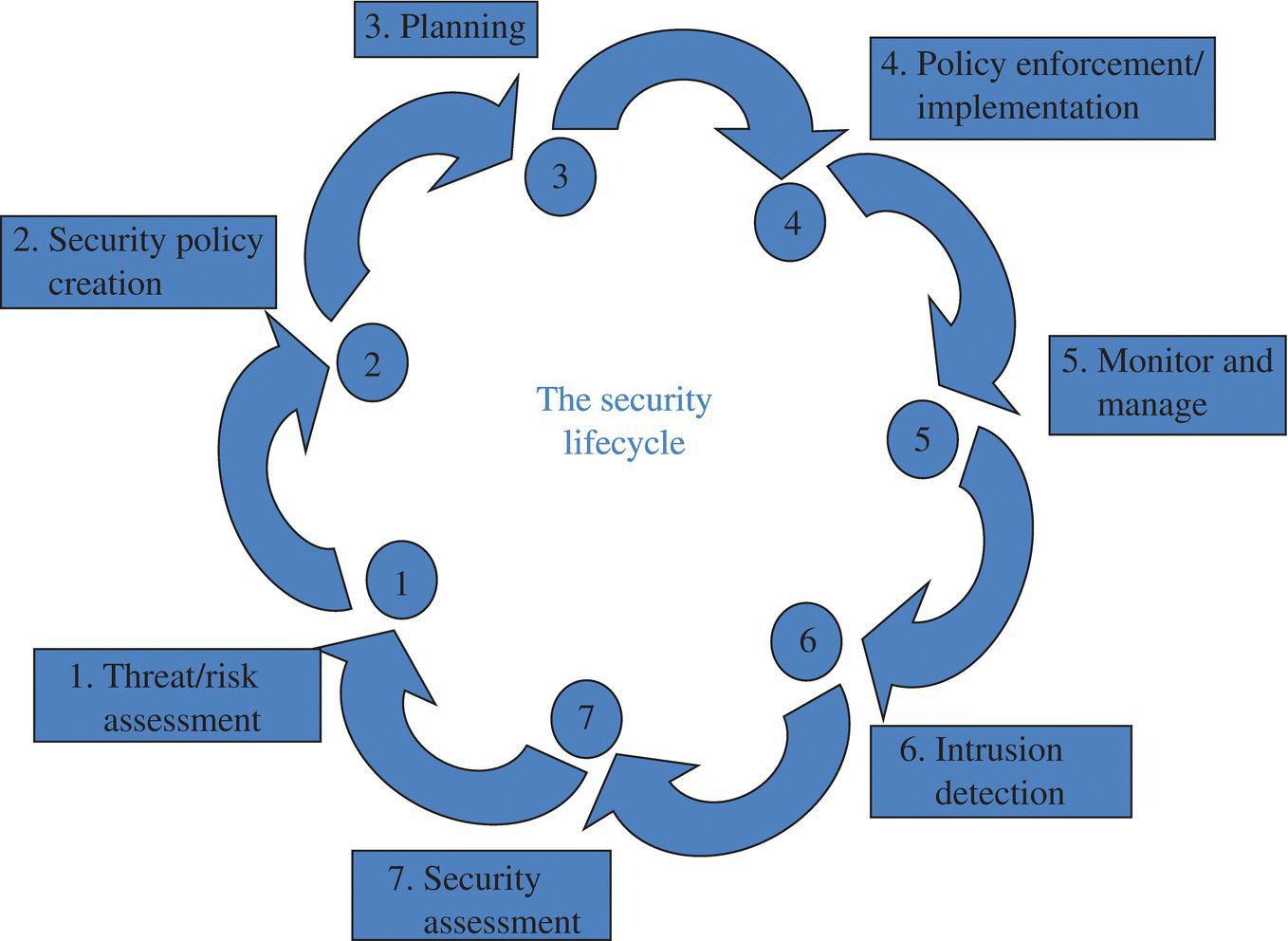
Figure 6.1 The security life cycle.
The process of cyber security is continuous; it must be continuously updated. As new programs and cyber intruders develop and exploit new vulnerabilities in computer programs and systems, the network defenders have a continuous struggle to defeat their attempts. High-profile attacks by China and private hackers have exposed vulnerability in even the best and most secure ...
Get Industrial Security: Managing Security in the 21st Century now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

