Chapter 2. Security
Adding software on top of machines and connecting them to networks creates tempting targets for malicious hackers. The evolution of industrial internet security is much like the evolution of PC security: many systems that are now being networked have historically enjoyed security by isolation, and, just as the original generation of PC operating systems didn’t anticipate connections to the Internet, many industrial systems were not built with outside contact in mind.
The inherent scalability of software means that a single exploit can propagate fast; once discovered, an exploit can be used against lots of machines. Think of a car’s odometer: the move to digital mileage counts, stored in software, makes it more difficult to tamper with the readout, but it expands the prospective target of an exploit from just one car (for mechanical odometers) to every car that uses the same software.
Tools like Shodan[9], a search engine for the Internet of Things, and Digital Bond’s Basecamp[10], a database of industrial control exploits, illustrate the scale of the industrial internet and its vulnerabilities.
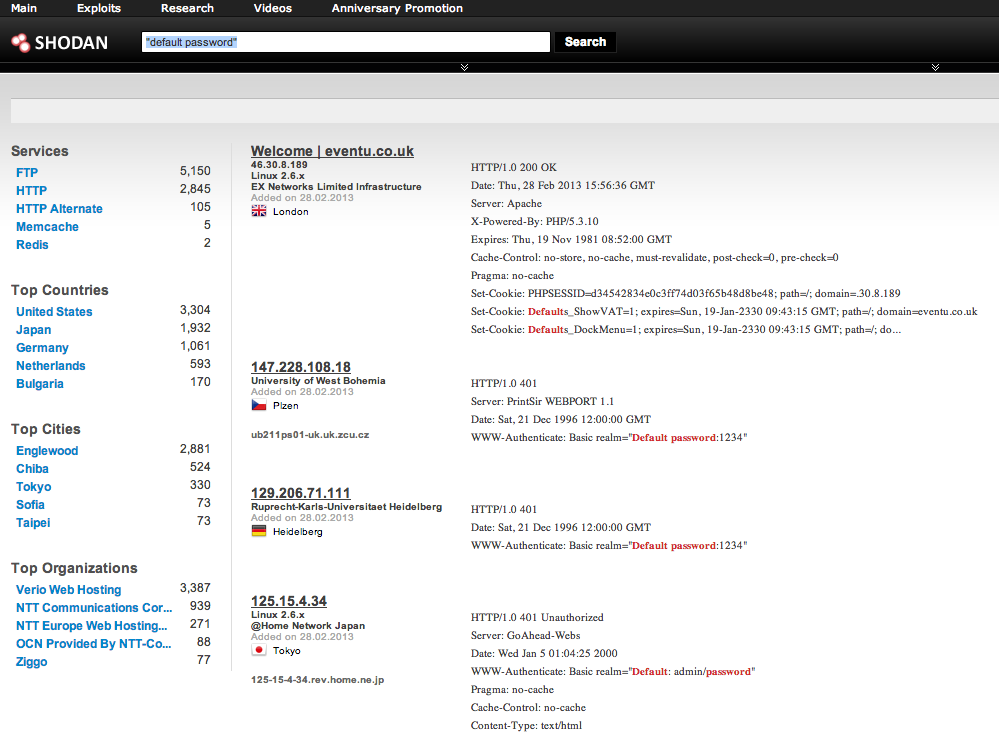
Shodan is a search engine for Internet-connected devices, including some industrial control systems and Internet switches. Here it reveals several computers that return a default password field in their HTTP responses.
Industrial-control security is a fast-growing discipline ...
Get Industrial Internet now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

