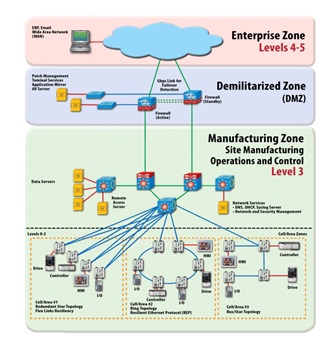
Much as physical security is about restricting authorized access to physical areas and assets of the ICS, network security is about restricting access to logical areas of the ICS network. The idea is to divide the network into security zones, using an IDMZ, applying firewall rules, setting up access control lists, and implementing Intrusion Detection Systems (IDS) to fence off more sensitive parts (more secure zones) of the network from less secure zones. By tightly controlling and monitoring traffic traversing the security zones, anomalies can be detected and handled effectively.