As a last exercise before we close the book on Modbus, I am going to show how Scapy can use a captured packet as a starting point. If you recall the Nmap script, Modbus-discover.nse will send packets containing the function codes that request the Modbus server for information. Let's run the script again and capture the packets with Wireshark:
# nmap 192.168.179.131 -p 502 --script Modbus-discover.nse
It is the first request packet that we are going to use; right-click on it and go to Copy | ...as a Hex Stream:
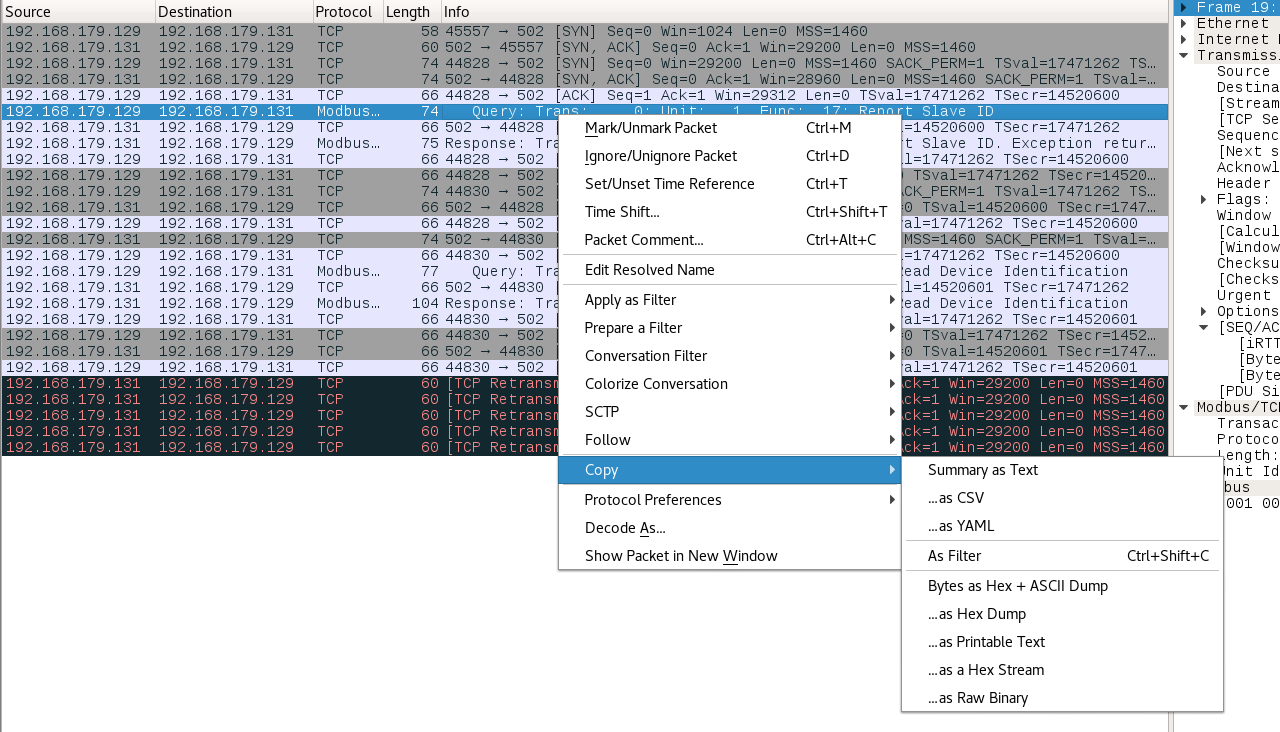
Now start Scapy in a Terminal and run the following command:
>>> from Modbus.Modbus import *>>> import ...

