8.7. Programmatic login
When you want to implement your own login mechanism for your application, you may want to use JAAS and implement the required programmatic login.
Figure 8-8 shows the activity diagram for JAAS and how the different components are working together during a login process.
Figure 8-8. JAAS sequence diagram
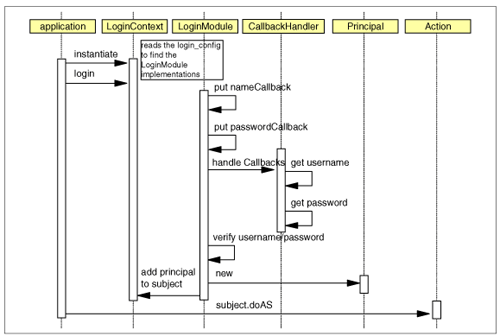
The step-by-step process is described below:
The application starts the login process using JAAS.
The LoginContext is initialized.
During the login process, executed in the LoginContext, a Principal will be authenticated using the specified callback handler.
If the authentication was successful the LoginContext commits ...
Get IBM WebSphere V5.0 Security: WebSphere Handbook Series now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

