98 IBM CSM to IBM Systems Director Transformation Guide
Each AIX machine runs the RMC daemon rmcd, which is under SRC control.
The CtSec library starts the Cluster Authentication Service (CAS) daemon ctcasd on
demand when CtSec authentication is required. This daemon is also under SRC control.
Both are in the SRC group rsct.
The data that CSM stores in the system registry is managed through CSM-specific resource
managers and mainly resides on the management server. However, the RMC/SR
infrastructure can be exploited in many different ways, such as on individual machines.
Furthermore, RMC itself only provides an abstract view of resource classes and resource
instances. Different resource managers (RMs) provide access to the actual resources. Some
RMs are shipped with RSCT, while other components such as CSM implement their own
RMs. All RMs are under SRC control, in the SRC group rsct_rm. Running the command
lssrc -ls ctrmc will produce a detailed status report of the RMC subsystem, including the
active resource managers.
For more detailed information about RSCT and CSM, visit the Libraries Related to Cluster
Products section at the IBM Cluster Products information center website or the following
books.
SA23-1343-05 - CSM for AIX and Linux V1.7.1: Administration Guide
SA23-1344-05 - CSM for AIX and Linux V1.7.1: Planning and Installation Guide
SA22-7889-20 - RSCT: Administration Guide
SA22-7890-20 - RSCT for AIX: Technical Reference
4.4.2 Authentication and authorization when using IBM Systems Director
Systems Director offers a number of security features by using the authentication and user
administration provided. System administrators can specify user privileges for specific tasks
of resources. This user registry integration, integrity and secure data transmission are key
elements of the basic security model. Systems Director is controlled by two basic
independent processes, authentication and authorization.
Authentication
Systems Director uses authentication to determine the identity of the user. It verifies and
validates that identity. When using default registry settings users are authenticated using their
user IDs and passwords, which reside locally on the operation which is then verified against
the information stored in the user registry that is configured by Systems Director. It also uses
the group information. Besides default registry, options like Lightweight Directory Access
Protocol (LDAP) are also supported,
Authorization
Systems Director uses authorization to validate the roles and privleges of the authenticated
user. This occurs when already authenticated users use Systems Director to perform a
specific task on a resource. If the task or role exists and contains the authorization necessary
to complete the task or role that was speficied, then it proceeds. If a user wants to run
additional commands using smcli then additional roles need to be authorized.
In conjunction with this, Systems Director heavily relies on role-based access control (RBAC),
which allows administrators to create and customize sets of permissions, also known as
roles, and assign them to individual users or groups; refer to Figure 4-12.
Chapter 4. Functional comparison 99
Figure 4-12 Basic IBM Systems Director communication topology
The Systems Director Server by default uses a Secure Sockets Layer (SSL) for the
communication between the web management console and the server, and depending on its
target such as agent, network devices, or storage devices, different communication types may
be utilized. IBM Systems Director stores all of its data in a database repository, which also
contains credentials such as userid and passwords that are used for accessing remote
systems. All of the sensitive data, including credentials, is encrypted using the 3DES
algorithm.
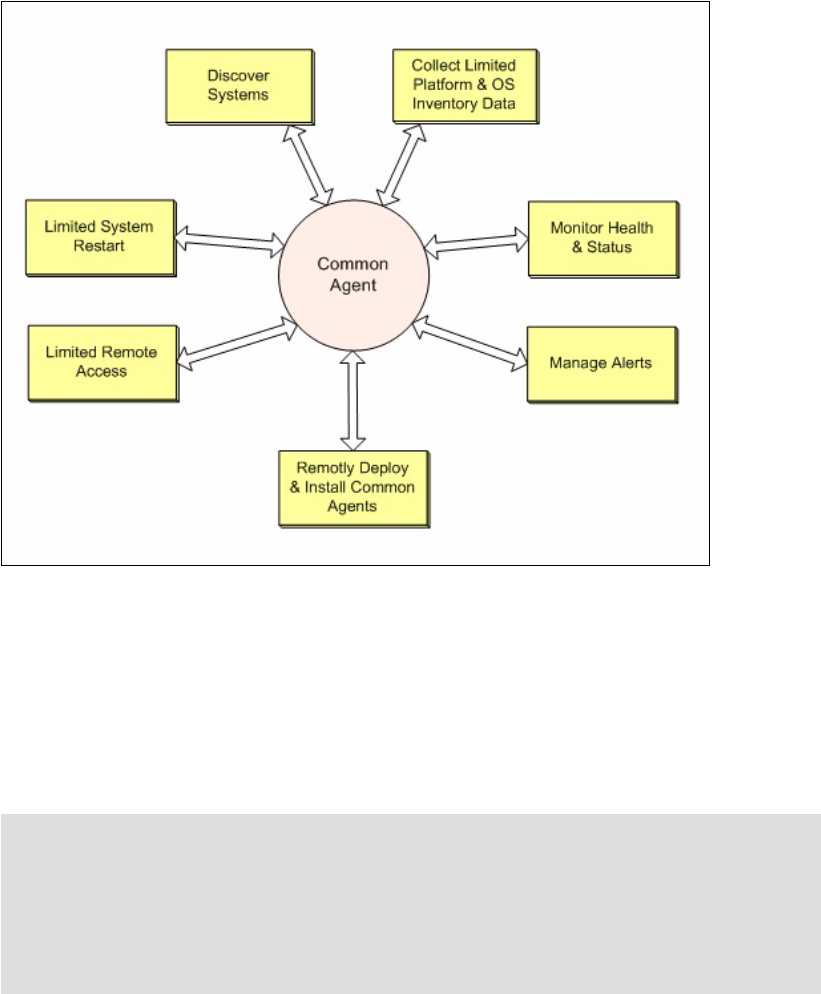
Using the agent manager
The agent manager provides the authentication and authorization for installed common agent
resources and maintains a registry of configuration information about the common agent
managed systems. It also provides the core agent manager functionality services:
Service catalog
Credential manager
Agent registry
Querying service
Notes:
The default certificate used by Systems Director should be replaced by either a
self-signed certificate or by using one signed by a certificate authority (CA). This is to
ensure data privacy. The keystore password should also be changed.
An SSH server is not provided by the Systems Director Server software, so use the
SSH server included by the operating system or a third party.
Get IBM CSM to IBM Systems Director Transformation Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

