Asymmetric Cryptography
With asymmetric cryptography, often referred to as public key cryptography, a key pair is employed that consists of both a public key and a private key. A message encrypted with the public key of a pair can only be decrypted with the corresponding private key. Conversely, a message encrypted with the private key can only be decrypted with the corresponding public key. For this reason, it may be clearer to visualize public and private keys as each playing the role of both a key and a lock, such as shown in Figure 18.2.
Figure 18.2. Asymmetric cryptography employs both a public key and a private key.
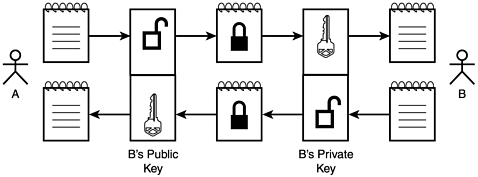
Because of this relationship, ...
Get HTTP Developer’s Handbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

