Message Injection
Once a key stream is known, a new message can be constructed by taking the new plain text and XORing it with the known key stream to create a new, forged cipher text. Again, since the 802.11 standard does not require the IV to change with every packet, each device must accept reused IVs.
For example, let's say we know the plain text and cipher text for a particular message. We could use this information to derive the key stream (Figure 3.5)
Figure 3.5. Deriving a key stream.
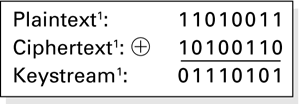
Using the key stream, we could take our own plain text and use the key stream to forge a new cipher text. This packet could then be injected into the network ...
Get How Secure Is Your Wireless Network? Safeguarding Your Wi-Fi LAN now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

