Dueling <auth-constraint> elements
If two or more <security-constraint> elements have partially or fully overlapping <web-resource-collection> elements, here’s how the container resolves access to the overlapping resources. A and B refer to the DD on the previous page.
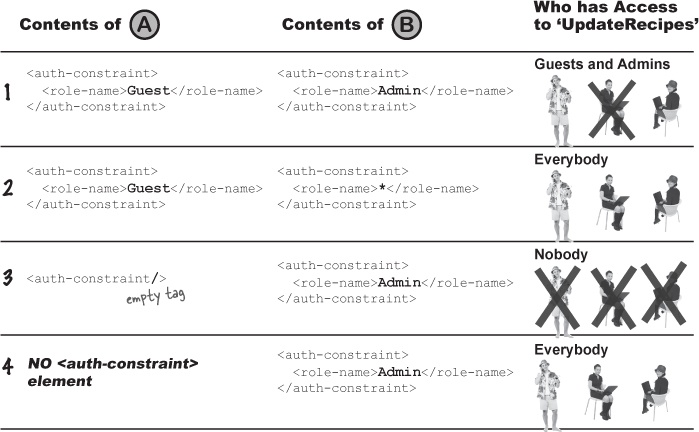
Rules for interpreting this table:
1 When combining individual role names, all of the role names listed will be allowed.
2 A role name of “ * “ combines with anything else to allow access to everybody.
3 An empty <auth-constraint> tag combines with anything else to allow access to nobody! In other words, an empty <auth-constraint> is always the final word!
4 If one of the <security-constraint> elements has no <auth-constraint> element, it combines with anything else to allow access to everybody.
Note
When two different nonempty <auth-constraint> elements apply to the same constrained resource, access is granted to the union of all roles from both of the <auth-constraint> elements.
Get Head First Servlets and JSP, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

