How multiple <security-constraint> elements interact
Just when you thought you had <security-constraint> figured out, you realize that multiple <security-constraint> elements might conflict. Look at the DD fragments below, and imagine the different combinations of <auth-constraint> configurations that might be used. What happens, for example, if one <security-constraint> denies access while another <security-constraint> explicitly grants access... to the same constrained resource, for the same role? Which <security-constraint> wins? The table on the opposite page has all the answers.
Multiple <security-constraint> elements with the same (or partly-matching) URL patterns and <http-method> elements:
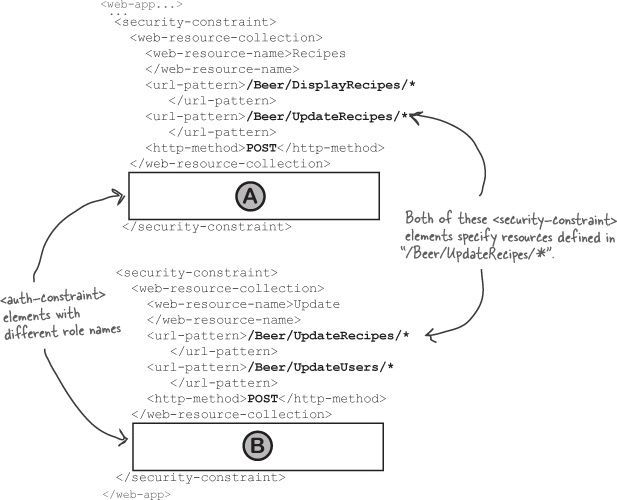
How should the container handle authorization when the same resource is used by more than one <security-constraint>?
Get Head First Servlets and JSP, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

