Chapter 7. Routing Protocols: It’s a Matter of Protocol

To build big networks, you need to use routers and they have to talk to each other.
Routers need to exchange routes with each other. They use various routing protocols to exchange routes. In the chapter, you will first see how to manually enter a route, then you will learn how to implement the simple RIP routing protocol. Finally you will learn how to setup EIGRP, an advanced routing protocol.
Houston, we have a problem...
So far, you’ve successfully hooked up the Moonbase network so that it can communicate with the ISS. There’s just one problem: there are actually 20 bases on the moon, and all the different moonbases need to keep in contact with each other through their network links in case they get into trouble. So is this possible?
When the international community started building the moonbases, they wisely decided to run fiber optic cables to all of the different moonbases. Each moonbase is directly connected to at least one other moonbase, and indirectly connected to all the others through the web of fiber optic cables. As an example, Moonbase 1 is directly connected to three other moonbases, and indirectly connected to all 20 others.
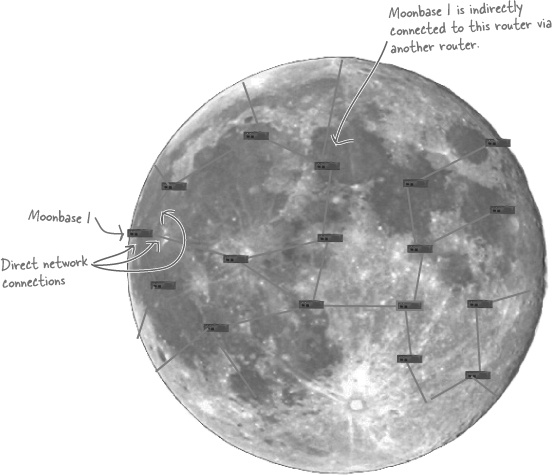
The Moonbase 1 router is able to send packets to the moonbases it’s directly connected to, but ...
Get Head First Networking now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

