Part V
Hacking Applications
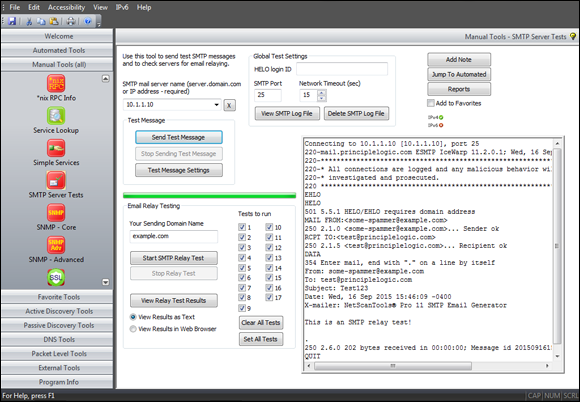
In this part …
Well, this book has covered all the essential security tests from the nontechnical to the network and on to mobile devices and operating systems. What I haven’t yet covered are the applications that run on top of all this as well as database servers and storage systems that ensure the data is available when we need it.
The first chapter in this part covers various messaging system hacks and countermeasures for e-mail and Voice over IP (VoIP) systems. Next, this part looks at web exploits, along with some countermeasures to secure websites and applications from the elements. Finally, this part covers attacks against database servers and storage systems. It covers both structured data found in various database systems and unstructured data, otherwise known as files scattered across the network waiting to be exploited.
Get Hacking For Dummies, 5th Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
 Read even more great Dummies content at
Read even more great Dummies content at 
