Security Solution Evolution
Takings these trends one step further, here we provide a general overview of the current and future technologies. These solutions span security for the gateway/ server/client, applications security, and overall management of your information security program. Figure 8-5 provides a summary of these solutions.
Figure 8-5. Solution evolution.
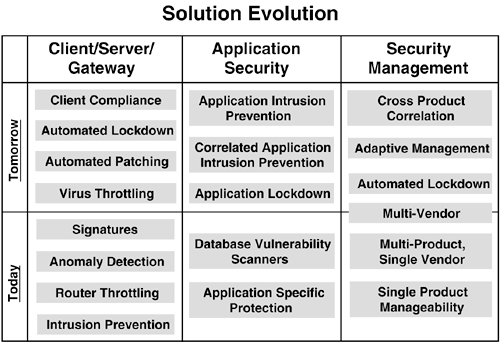
Gateway/Server/Client Security—Today
Existing technology relies upon two major methods for protection: signatures and anomaly detection. Signatures identify an attack or suspicious file based upon a known differentiating property. A header section of an email message with the words ...
Get Executive Guide to Information Security, The: Threats, Challenges, and Solutions now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

