Process—Strategy
Information security policies, standards, and procedures are different documents that all need to work together to support the process component of an information security program. Figure 5-2 shows an overview of these documents.
Figure 5-2. Information security program process overview.
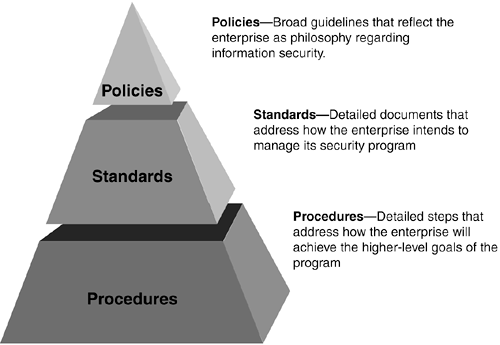
Each enterprise has unique factors that it needs to consider when developing its own processes; these include company size, complexity, and industry.
Things to Consider
Creating an effective security policy is a balancing act—employees must have access to the information assets they need to do their jobs and stay productive. At the same time, ...
Get Executive Guide to Information Security, The: Threats, Challenges, and Solutions now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

