Chapter 1. Introduction
In this chapter:
Computer systems are used for many different purposes in business today. These range from keeping personal to-do lists to developing business-critical applications in banks. Applications are often categorized by their purpose. For example:
- Personal productivity and groupware
The use of Personal Computers (PCs) for word processing, electronic mail (email), and document sharing using a Local Area Network (LAN).
- Design and development
Computer-aided design and software development.
- Manufacturing and production
Monitoring and control applications in factories.
- Business intelligence
Data warehousing applications used to aid decision-making, arising from powerful, large-scale databases.
- Business operations
Business operations applications (sometimes called line of business applications) that “transact the business” of a company—in other words, they perform business transactions on behalf of the company. This is not limited to cash-for-goods transactions. It can include any buyer/supplier transaction that can be translated into a digital format, as well as internal business processes dealing with company resources. For example:
Credit card transactions
Cash transactions from a bank’s Automatic Teller Machine (ATM) or supermarket cash dispenser
Stock market transactions for a stock exchange or brokerage
Information transactions for collecting, collating, and distributing news—such as the results and medal tables for the Olympic Games
Payroll transactions (essential for the smooth operation of any corporation)
Logistics transactions, such as the scheduling of vehicles in a transportation company
Voice application transactions (“Press 1 to enter your meter reading….”) for a computer integrated telephony system
Sales transactions for companies doing business through the Internet
Business applications are crucial to many large and medium-sized companies. For such companies, doing business without these applications would be unthinkable; a bank that lost its computerized account records would cease trading. Many, if not most, of the largest business applications around the world run on CICS.
The Essentials of a Business Application
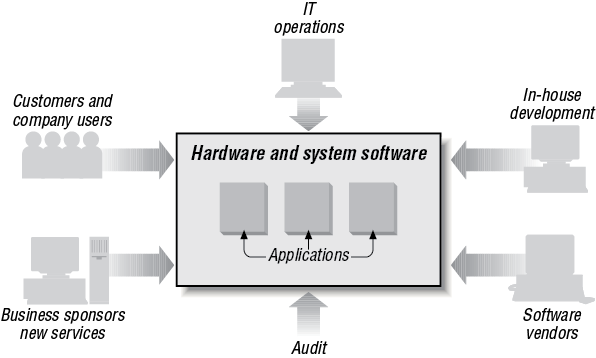
Even though the computer is at its center, a business application is focused on people. It is a human system as much as a computer system. The purpose of a business application is to keep accurate, up-to-date, and secure operational business information and deliver it rapidly to the users of the application. There are a number of key features that any business application needs. They have to be fast, accurate, secure, and auditable. In addition, the information has to be up to date and available to multiple users across a company, its suppliers, customers, and business partners. A model of the relationship between computers and people is shown in Figure 1-1.
Division of Responsibilities
Accuracy (in the sense of adhering to the intent of the business) depends on the computer system being controlled appropriately; that is, having clear lines of responsibility and division of responsibilities. It is essential to have organizational responsibilities that the system itself monitors and enforces. To this end, business applications broadly separate system development, system operations, and system use with checks and balances. These may be as official as a system audit. There are, of course, many subdivisions of these roles; for example, system development may be subdivided into architecture, design, programming, and testing.
Division of responsibility ensures that different groups of people involved with an application are unable to take advantage of their situations. Consider a payroll application, it should be impossible for payroll clerks to update their own salaries without being monitored; programmers would have built into the program an audit log that is checked by the audit department. Similarly, the program should include a log of all software updates to ensure that system administrators are unable to make fraudulent changes to the program without trace.
Lifecycle Requirements
Business applications define the business rules that control the delivery and update of critical data; therefore, they require support throughout their lifecycle. The stages of a lifecycle include:
- Design
Design user interfaces that meet users’ needs; design for growth and extension; design to build complex applications with many features and capabilities.
- Develop
Develop efficiently, using modern tools and techniques.
- Test
Test thoroughly and efficiently to find problems and track down causes of problems.
- Update
Update in such a way as not to disrupt the existing version when upgrading to a new version.
Technical Requirements
In addition to lifecycle requirements, business applications must also meet a set of general technical requirements:
- Accessibility
The application can be used from any appropriate place on the network.
- Availability
The application is available for use by authorized persons at all designated times; it does not need to be shut down for routine maintenance and can be upgraded without interruption.
- Communication
Rapid communication is possible between distributed parts of the application.
- Manageability
Systems administrators can monitor the application to detect problems, and can take corrective action before users complain.
- Prioritized use of the hardware
A management capability should be in place to determine how much the machines are used, so that the workload can be distributed evenly.
- Rapid response
The response time for end users is appropriate (which usually means short!).
- Reliability
The application is not expected to fail, but if it does, it provides diagnostic information to help identify the cause of the failure.
- Recoverability
The application restarts quickly after a failure, without loss of information or of data integrity.
- Scaleability
The application can support as many users as needed without slowing down excessively or requiring excessive resources.
- Security
The application includes the ability to control who can use it, and which actions the users can perform.
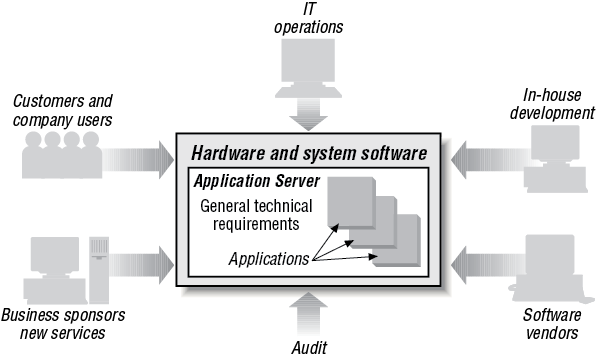
CICS was originally seen as a transaction processing system. Indeed behind the scenes this is a lot of what it is doing. But, like a lot of middleware, CICS comes to life by virtue of the many applications and operating systems that it supports. It not only provides an extensive Application Programming Interface (API), but it also controls the resources behind the applications; for example, security, databases, files, programs, transactions and so on, that the applications use. Hence, as CICS has evolved, describing it as an application server gives a much truer picture of its role today. In Figure 1-1 we see a loose arrangement of applications, which largely function independently of each other. Figure 1-2, on the other hand, draws those applications together so that there can be, for example, shared resources distributed across a computer network. To support the division of responsibilities, lifecycle requirements, and general technical requirements, an application server is required to manage the business applications. This is where CICS fits in. IBM’s product CICS is an application server.
If you have key applications that run 24 hours a day for 7 days a week and if your business requires that applications can be recovered completely after failure, you have good reason to move to CICS. If your business already uses CICS, extending your CICS system provides an integrated solution for your ever-increasing business requirements.
Business Applications as Creators of Value
Historically, companies adopted and became dependent upon business applications because of the reduced costs, improved accuracy, and timeliness of information achieved by transferring key operational data for their business onto computers. Today’s business applications must enable rapid development of modern services and must be able to exploit new hardware and software technology for competitive advantage. The latest technology is, of course, the Internet.
Responsibility for developing and managing business applications has changed from being a separate business function to a central part of competitive strategy—from merely boosting operational efficiency to profoundly changing the nature of products, services, and business processes.
The ability to adapt and extend applications has become increasingly important when launching new products and services for maximum advantage. This applies when you’re bringing your own ideas to market quickly, and bettering your competitor’s offerings. Companies that are today maximizing the potential of Information Technology (IT) to create value are taking radical approaches to developing the systems necessary. The key features are:
Use of cross-functional teams having responsibility to the business—especially between central and departmental IT groups—because command and control management needs to include all interested parties.
Maximizing the amount of information held by IT networks.
Maximizing connectivity to provide information where it is needed.
Selective use of contracted skills—for example, in web design—rather than attempting to maintain in-house skills across the entire range of technologies.
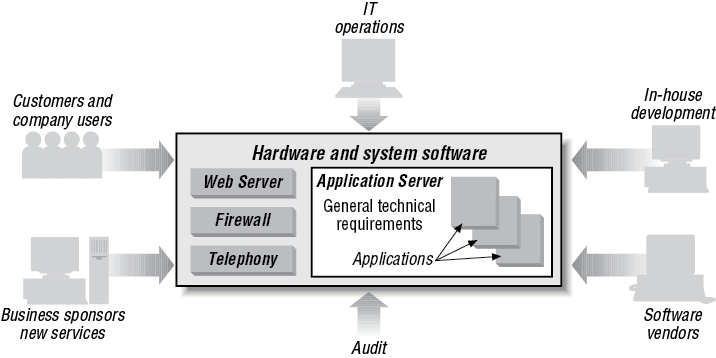
At the heart of all successful implementations of this approach are the business applications that have been running the business for years—but expanded with more data, applications, processing power and connectivity, and augmented with technologies such as web servers and computer telephony integration. In Figure 1-2, we emphasized how CICS as an application server draws together the applications and resources of a computer system. Figure 1-3 shows application servers have to interact with other systems, both software, for example, web servers and firewalls, and hardware, for example, telephony. Interconnectivity between operating systems and hardware is critical. As a result, a modern business application looks something like that shown in Figure 1-3.
Using CICS for Business Applications
This book shows you how the CICS environment enables you to build a business application consisting of a varied set of components. By satisfying the essentials of a modern business application, CICS provides solutions for your business that improve efficiency, competitiveness, and productivity. Additionally, CICS can help your business implement an e-business strategy—competing in a global marketplace for worldwide customers who find you and trade with you electronically using the World Wide Web.
Examples of Business Applications That Use CICS
CICS is used in many different ways by many different businesses. Let’s look at a few examples in which CICS is used to help businesses. These examples are based on real customers. For a much longer list of case studies, go to the CICS home page at http://www.ibm.com/software/ts/cics/ and select case studies.
- Financial services (banking, securities, investment services, and insurance)
Company A provides a wide range of services, from consumer banking to securities brokerage. Transaction processing is essential in providing these services. The company uses CICS to produce timely, accurate financial information, in the knowledge that if problems arise they can be resolved easily. Recovery of data is critical. There are a large number of vital CICS applications, written in COBOL many years ago, which Company A doesn’t want to give up. But, at the same time, it wants to embrace the World Wide Web and spread some of its applications to workstations and Unix systems. The requirement is to retain the reliability and integrity of its mainframe-based systems while meeting the need from internal and external customers for more flexible, distributed processing.
With CICS, this is not a problem. The company’s IT managers can use their existing COBOL programs, retaining all the existing CICS transactions. In addition, they decide to use their current files as their database and then use the CICS External Call Interface (ECI) as a gateway for non-CICS servers to gain access to their business data. This ensures that they extend their business to the distributed environment. Having done that, they are then able to implement a web-trading application very quickly. Six months later, they were processing 60,000 transactions per day in this environment, on top of a peak load of 1,200 CICS transactions per second. The key to their success was to build an infrastructure that enabled them to extend their mainframe processing to the distributed environment.
Bank B, which provides full banking sevices with 800 branches online connected with distributed CICS servers, processes 30 million transactions a day using all the business attributes of CICS: reliability, recoverability, scalability, security, and so on.
- Retail
The distributed processing model can be extended to the retail market. Take the case of Company C, which runs a chain of pharmacies across the country. With the help of CICS, a data sharing system is set up for the processing of customer prescriptions. The system allows customers to input their information (name, address, specific allergies, and so on) and allows for detailed online checking to ensure that the drugs being dispensed are right for the customer. The information required to give the complete picture can be built up on the pharmacist’s display in real time using CICS and DB2.
- Distribution
The distributed processing model can also be used to track packages, from the time that they leave manufacturing to their final delivery. In Company D, drivers using hand-held devices record the delivery of the packages, and this information is sent to the server and made available to the anxious customer. The flexibility and variety of modes to input information—together with the ability to instantly deliver that information to the place it is wanted—are the true benefits of this real-time system.
- News and information
At the Olympics, there is a huge amount of computer processing. Two of the main requirements are controlling the movements and providing adequate security for the competitors and officials, and dealing with the results from thousands of events.
During the games, more than 150,000 competitors and officials require access to 80 venues and facilities. Part of the process is a timely, accurate procedure for registering, authenticating, and badging the competitors and officials, and using those badges as a means to manage access to venues, thus ensuring the safety and security of the events. The badging process alone involves 5,000 complex transactions a day, together with background transactions involving 100–150 concurrent users, and emphasizes the need for a system that supports a high transaction throughput in a distributed environment.
The results system gathers, calculates, and tabulates information from the timing, scoring, and judging stations. The results are immediately sent out to the venue scoreboards and interactive touch screens, where they are checked by judges. They are then transferred to the mainframe for distribution to other venues, to printers and to the massed ranks of sports journalists. The Commentator Information System (CIS) communicates directly with the mainframe and PCs that run the results systems. A touch screen allows commentators to pull up information about different sports and participants, allowing a commentator in one venue to comment on several events taking place elsewhere. Altogether the data collection system contains over one million data fields of researched, validated historical results, 20,000 biographies and over 30,000 paragraphs of text—a total of 60 gigabytes of information.
CICS works as an integral part of both systems, people management and processing of results.
Get Designing and Programming CICS Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.