9.1 LUCIFER
Horst Feistel's paper [Feistel, 1973] described the role cryptography might play in providing privacy in computer systems. The importance of this paper cannot be underestimated; first, it suggested a template for the design of cryptographic algorithms and second, it challenged the Government's undisputed role as master in the area of cryptology. It initiated a new era in cryptography that would lead to public-key cryptography. It was also of benefit to NSA, forcing it to re-examine its relationship with universities and business organizations.
Feistel's paper described LUCIFER, a product block-cipher enciphering plaintext data in blocks of M bits:
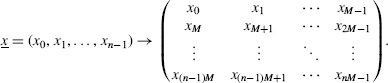
Feistel used the APL programming language to experiment with and test LUCIFER. The program was stored in an APL-workspace, the analogue of a PC/MAC-folder and a UNIX-directory. The APL implementation, available at this time, imposed a limit on the number of letters in a workspace name. Feistel's original choice of DEMONSTRATION for the workspace name had to be shortened to DEMON; ultimately, someone suggested the sexier name LUCIFER.
A description of one version of LUCIFER may be found in Sorkin's paper [1984]. Outerbridge [1986] referred to LUCIFER as a Feistel-like block product cipher.

Figure 9.1 Horst Feistel (Courtesy of ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

