18.1 UNIX PASSWORD ENCIPHERMENT
A Log-In to a UNIX system requires the user to provide a password Pass(User_ID), which is hashed to Hass[Pass(User_ID)] and compared with the entries in the UNIX password file consisting of
![]()
where the number [n] is the length in characters (bytes). A cryptographic salt consists of approximately 4096 = 212 randomly chosen bits, which are used to further “mix up” the Hash(UserPass_ID). The UNIX crypt(3) command chooses the salt to be a pair of the characters
![]()
The original idea is due to George Purdy [1987], who proposed using a one-way function to
- Recalculate the Pass(User_ID) → Hash[Pass(User_ID)] during a log-in, and
- Compare the result in (1) with a stored value in the file /etc/passwd., which contains (User_Name, Salt(User_ID), Hash[Pass(User_ID)], User_ID)1 or if a shadow password implementation is being used (User_Name, Salt(User_ID), *, User_ID), signalling that Hash[Pass(User_ID)] is stored (encrypted) in another file.
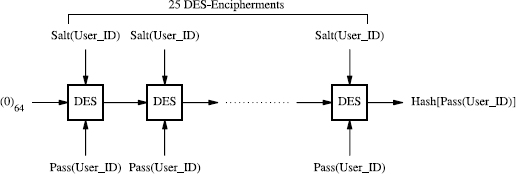
Figure 18.1 crypt(3) Computation of Hash[Pass(User_ID)].
Purdy suggested using polynomials over a prime modulus to construct the one-way function. There have been various implementations of the hash function. The crypt(3) has several ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

