13.7. Applications
In this section, we discuss the secondary spectrum access with LT codes based on []. In the secondary usage scenario, an SU selects a set of subchannels from the PU bands as discussed in Section 13.2. The SU is required to vacate the subchannel as soon as the corresponding PU becomes active on that subchannel. This forces the secondary user to loose packets on that subchannel. To compensate for the loss caused by the PU appearance, the source packets are encoded with LT codes. Let the secondary user have a message M of K packets to transmit. And let the LT decoder need at least N packets in order to recover original K packets with probability 1 – δ'. Then in order to compensate for the loss due to PU appearance, we add some more redundancy, say X, which depends on PU arrival probability p. If PU arrival is quite frequent then we need to use a high value of X, if PU arrives occasionally then a small value of X is sufficient.
As discussed in [], let one packet be transmitted per subchannel, then the total number of subchannels used by SU is Q = N + X, and this transmission will be successful only if at most X of the subchannels are lost due to PU appearance. Therefore, the probability of successful transmission for the secondary users is given by
Equation 13.5
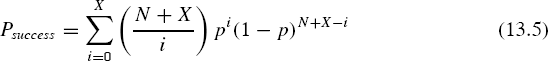
Let Tframe be the time required for transmission of each packet and W be the bandwidth per subchannel. ...
Get Cognitive Networks: Towards Self-Aware Networks now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

