When Sensors Detect Malicious Traffic
Based on how the sensor is configured and which mode it is in (IPS or IDS), the sensor can implement the actions described in Table 17-4.
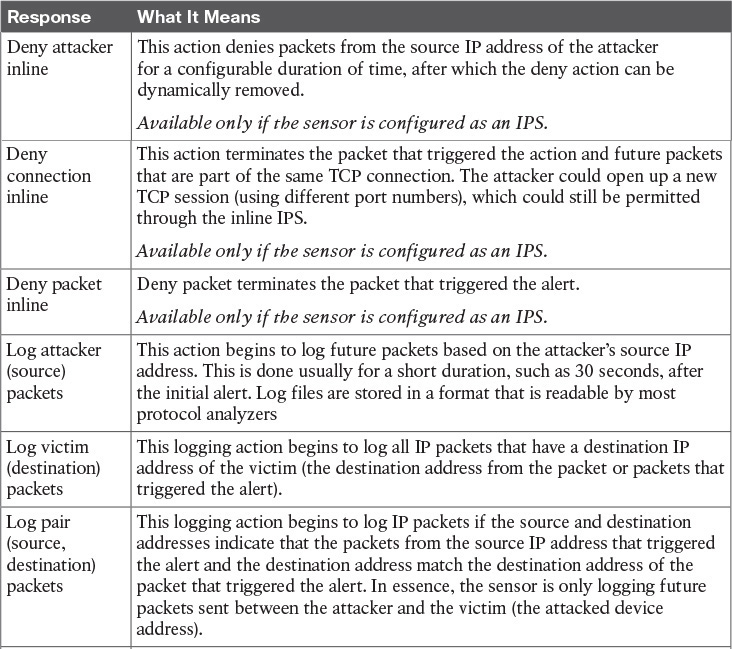

Table 17-4 Possible Sensor Responses to Detected Attacks
Note
All of the “deny” response options in Table 17-4 apply only to a sensor that is in IPS mode.
Get Santos:CCNA Sec 210-260 OCG now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

