Best Practices for Securing the Control Plane
Table 10-3 describes three ways to implement security of the control plane.
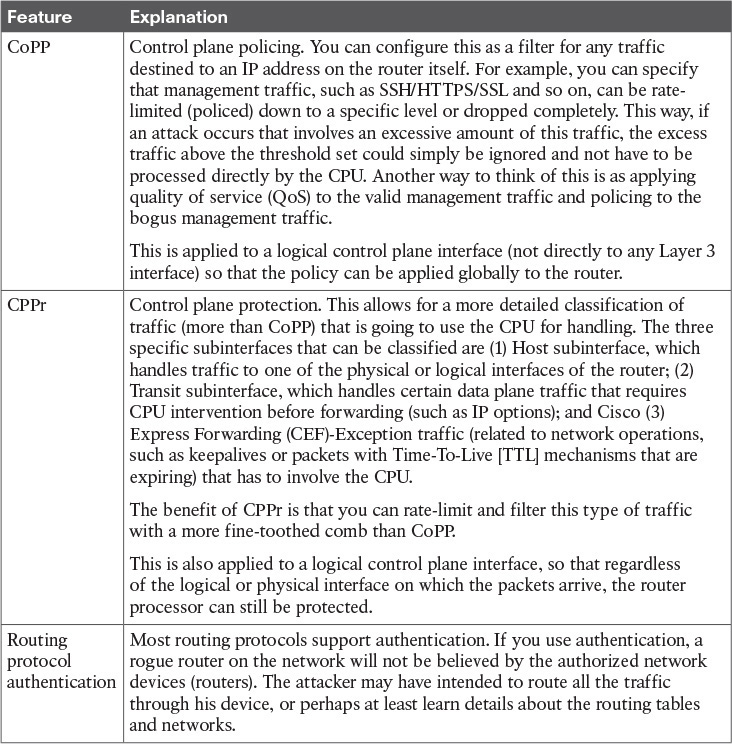
Table 10-3 Three Ways to Secure the Control Plane
Using CoPP or CPPr, you can specify which types of management traffic are acceptable at which levels. For example, you could decide and configure the router to believe that SSH is acceptable at 100 packets per second, syslog is acceptable at 200 packets per second, and so on. Traffic that exceeds the thresholds can be safely dropped if it is not from one of your specific ...
Get Santos:CCNA Sec 210-260 OCG now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

