The SIP dialog flow
Let's examine this message sequence between two user agents as shown in the following figure. You can see several other flows associated with the session establishment in RFC 3665:
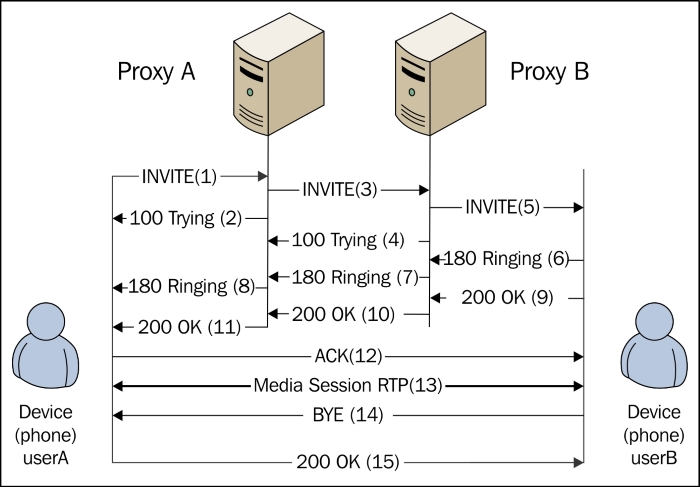
The messages are labeled in sequence. In this example, userA uses an IP phone to call another IP phone over the network. To complete the call, two SIP proxies are used.
The userA calls userB using its SIP identity called the SIP URI. The URI is similar to an e-mail address, such as <sip:userA@sip.com>. A secure SIP URI can be used too, such as <sips:userA@sip.com>. A call made using sips: (Secure SIP) will use a secure transport, Transport Layer Security ...
Get Building Telephony Systems with OpenSIPS - Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

