Manual exploitation
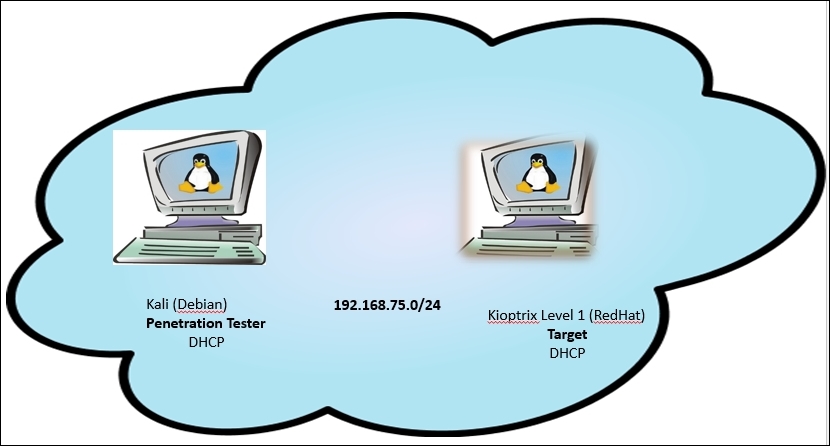
At this point, we should have two systems ready to go in our virtual environment:
- Our Kioptrix Level 1 machine, which will be our target
- Our Kali machine, which will be taking on the role of an attacker
Before we can start with exploitation, we need to determine our plan of attack. An example of our environment is shown in the following image:
Enumerating services
We will begin by locating the machine on our network using Nmap. Open up a new terminal session and type:
nmap -f -n -P0 -v -p- -T4 192.168.75.0/24
We instructed Nmap to scan all TCP ports for IPs on 192.168.75.X using fragmented packets. Here is an excerpt of the results: ...
Get Advanced Penetration Testing for Highly-Secured Environments - Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

