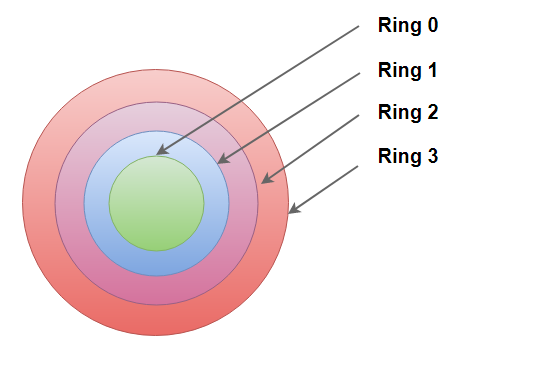
Most operating systems rely on a ring protection model. This model represents superposed conceptual rings varying from high to low privileges. There are four layers numbered from 0 to 3:
- Ring 3: This layer is the usual interaction layer, with the user normally in the user mode.
- Ring 2: This layer contains operations with low privilege.
- Ring 1: This is the layer of input/output operations.
- Ring 0: This is the most sensitive layer. The kernel resides in this layer.
Linux, like many recent operating systems, doesn't rely exactly on a ring protection mechanism, but it is working on a two-layer mode: user mode, and ...

