The first step is to check whether the host is alive. To verify the state of a machine, type nmap –sP <target>; the target could be an IP address, or a range of addresses:
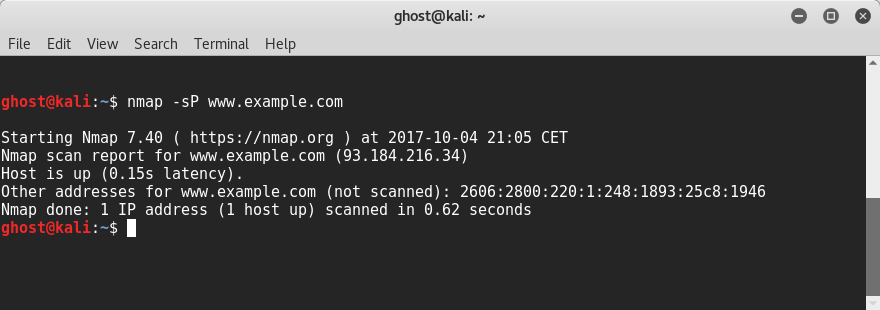
Basically, the check is using an ICMP request, thus, many network administrators are blocking this protocol request due to firewalls and intrusion detection systems. Hence, penetration testers could use TCP or UDP requests (don't worry; we will cover network aspects and protocols in the next chapter in a detailed way). To achieve it, you can use the nping utility:
Nmap has a great capability to detect operating systems, thanks to its huge database ...

