Data Corruption
Data corruptionâthe term strikes fear into the heart of the hardiest Access guru. Hopefully, the people who use your database will be well behaved, the network it sits on will remain reliable, and your database will never be in danger. But just in case life isnât that kind to you, itâs important to be prepared.
Data corruption is a catch-all term that describes what happens when part of a database file is damaged. Imagine Jessica Baxter is in the middle of applying a large update when a power failure hits (or an office prankster pulls out her network cable). The back-end database will be left in an invalid state, because only part of Jessicaâs information will have been successfully received. As a result, the record she was working with may be scrambled beyond recognition. And if youâre particularly unlucky, the problem can affect more than one record or even make the whole database act a little odd.
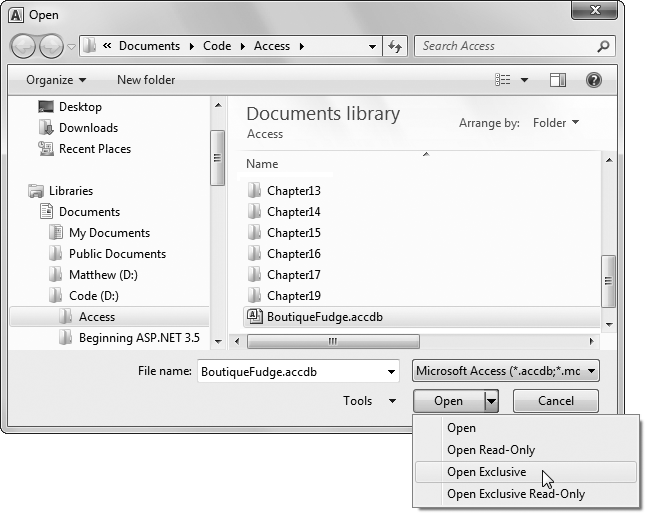
Figure 19-13. If you open a file in Exclusive mode, no one else can open it until you close it. If you open a file in Read-Only mode, you canât make any changes.
Diagnosing (and Fixing) Corrupt Databases
Every Access expert should have basic data corruption survival skills. First, you need to be able to spot when a database has gone bad. Here are some telltale signs:
Cryptic error messages that appear for no good reason, like âout of memory.â (Keep in mind ...
Get Access 2010: The Missing Manual now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

