Data in conventional networks travels across wired mediums. Coaxial cable, twisted pairs of copper wire, and strands of fiber optics have been the foundation for networks for many years. In order to view, interrupt, or manipulate the data being transmitted, the wires or switching equipment have to be physically accessed or compromised.
Tip
An attacker does not need to physically tap into wired communication in order to eavesdrop on it. Wired communication that uses electrons to transmit data (such as phone calls and 10BaseT Ethernet) radiates small amounts of electromagnetic energy. With highly sophisticated equipment, an attacker can reconstruct the original data stream from the radiated energy. The skill required to pull off this attack as well as the relative proximity the attack requires, however, makes it highly unlikely.
Restrictions on physical access to network cables have been a cornerstone of information security. While physical protection of cables obviously does not solve all the network security problems, it helps mitigate the risk of certain man-in-the-middle (MITM) attacks. Wires are relatively easy to keep physically secure. Placing wires inside of a controlled space such as a data center keeps the physical layer secure from the majority of attackers.
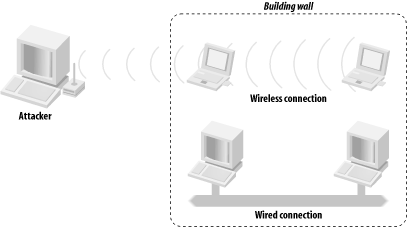
When using radio frequency (RF) communication channels such as a WLAN, users lose the fundamental physical security given to them by wires. WLANs use high frequency radio waves to transmit their data. These RF waves travel through the air and are difficult to physically constrain. RF waves can pass through walls, under cracks in doors, across streets, and into other buildings. Even if a wireless access point is located inside a physically controlled data center, the wireless data may leave the bounds of the data center into uncontrolled spaces, as shown in Figure 1-3.
Data on 802.11 networks can be intercepted from large distances if the attacker has line of sight. Peter Shipley, a security professional who performed some early research into wireless security, was able to eavesdrop on wireless networks in downtown San Francisco from the hills of Berkeley. That’s a distance of over 20 miles! For more info on Peter’s research, see his web site at http://www.dis.org/wl/maps/.
Due to the lack of physical control of where the wireless network data may end up, WLANs create special risks for users, administrators, and owners. Eavesdroppers many miles away may be able to intercept sensitive information or access machines that would be otherwise be protected by a firewall. When deploying a wireless network, the fundamental insecurity of the physical medium should drive the overall architecture.
Get 802.11 Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.