Chapter 15. Securing Communications
Several protocols for remote shell access were created in the 1970s and 80s, when security was not a concern; for example, Telnet in 1969, Remote Shell (rsh) in 1983, and Remote Login (rlogin) a bit later in 1991. These protocols do not have encryption, so the login and password information, as well as any commands launched by the client, are transported clearly along the network.
So anybody could sniff the traffic and read the data. If your network contains hubs, anybody connected to the hub can see all the traffic. For example, Figure 15-1 shows a packet capture of a short Telnet connection.
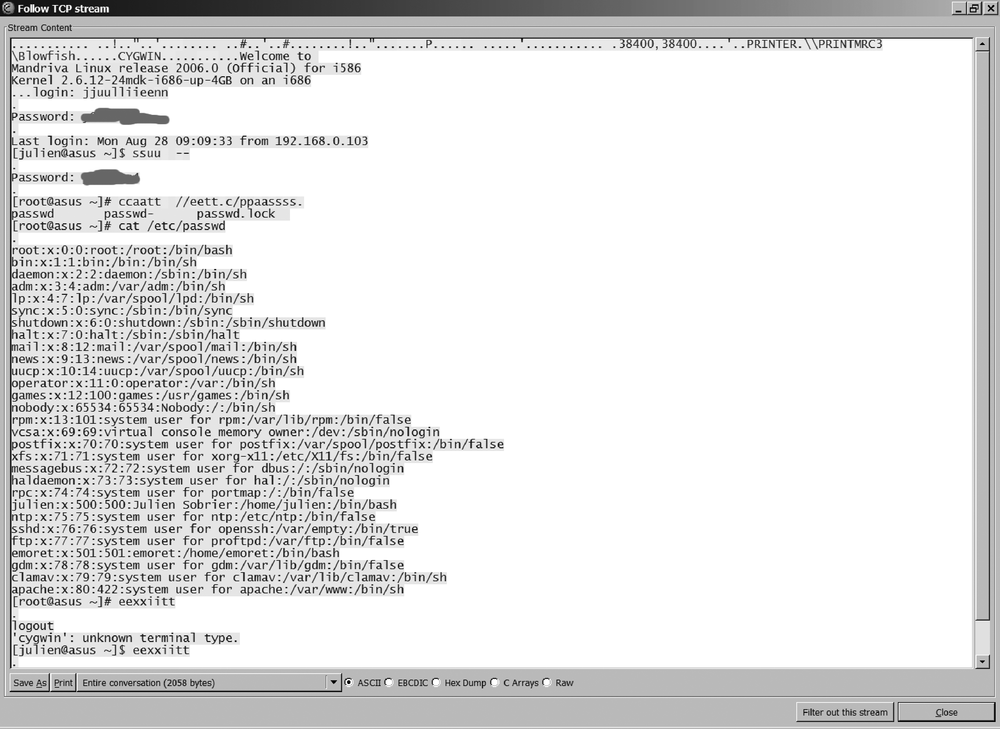
Figure 15-1. Passwords revealed by a Telnet session
Tip
A hub and a switch are network devices that connect several computers on a network. Hubs and switches have multiple ports where machines are connected. A switch transmits the incoming data on one port to another port based on the final destination. A hub forwards the data from one port to all of the other ports. Any computer connected to a hub can sniff all the data sent and received by any other computer connected on the same hub. This is why hubs are often banned from corporate networks.
Be careful with switches! Under certain circumstances, a switch can be forced into forwarding packets like a hub. A hacker with Layer 2 access to a switch could mount an attack against the switch by filling up its MAC cache ...
Get Security Power Tools now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

