A Simple Port Scan
- portscan.pcap
Attackers can use port scans to learn very critical information about a network. Using specialized port-scanning software, a hacker can attempt to connect to a device on a specified array of ports, such as 21 (FTP) and 80 (HTTP). With the information received from these scans, an attacker can find open ports that could allow access to your network. Think of an open port as a secret tunnel into a well-guarded castle. Once a hacker knows about one of these tunnels, he may very well be able to get in using the right bag of tricks. Figure 9-2, based on the capture portscan.pcap, shows a port scan at work.
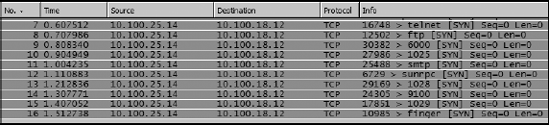
Figure 9-2. A ...
Get Practical Packet Analysis now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

