A Very Lightweight HTTPS Server and Client
An HTTPS server needs two stores for digital certificates:
- keystore
- A keystore contains digital certificates, including the certificates that an HTTPS server sends to clients during the peer authentication phase of the HTTPS handshake. When the server is challenged to establish its identity, the server can send one or more certificates for its keystore to the challenger. If peer authentication is truly mutual, then a client needs a keystore with the client’s own digital certificates, which can be sent to the server for verification.
- truststore
- A truststore is a keystore with a specified function: the truststore stores trusted certificates used to verify other certificates. When a host, server or client, receives a certificate to be verified, this received certificate can be compared against truststore entries. If the truststore does not contain such a certificate, the truststore may contain at least a certificate from a CA such as VeriSign, whose digital signature is on the received certificate.
Although the keystore and the truststore differ in core purpose (see Figure 6-6), one and the same file can function as both keystore and truststore, and, in development, this option is attractively simple.
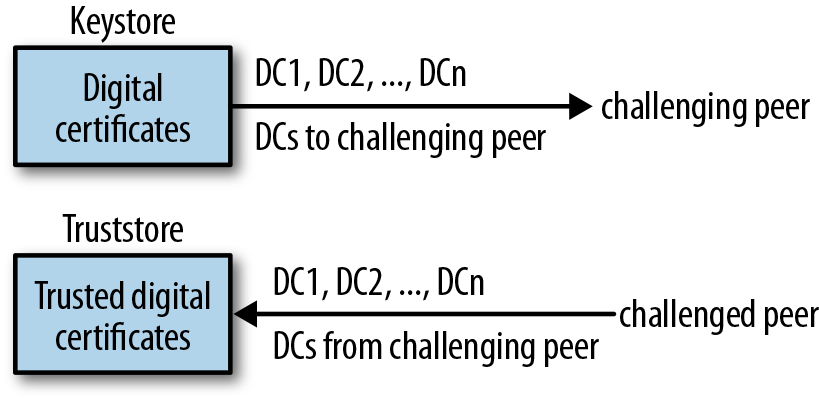
Figure 6-6. A depiction of how a keystore and a truststore function
In fleshing out these and related details about HTTPS security, the HttpsPublisher ...
Get Java Web Services: Up and Running, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

